Learn how organizations can leverage OSINT to detect early warning signs of both physical and cyber threats, enhancing employee and event safety through proactive risk management.
Modern threats are more dynamic and less predictable than those that occurred in the past. In the context of corporate environments, they are not only vulnerable to cyber incidents like phishing, ransomware and APT attacks but also to targeted physical attacks, protests, or espionage from other competitors or state-backed organizations. Public events, particularly high-profile or politically sensitive gatherings such as during election campaigns, face risks from terrorism, violent activists, or even lone wolf actors.
Threat actors commonly collaborate and communicate these threats in advance through open online channels such as forums, social media, blogs, pastebin websites and leaked databases. Ignoring these signals can lead to blind spots that compromise security, and here comes the role of OSINT: to discover these indicators in advance and prevent them from happening.
OSINT as a proactive defense layer in corporate environments
OSINT provides a cost-effective and scalable means to monitor different types of threats surrounding corporate works and help them mitigate potential threats before they mature. OSINT key applications in this field appear in the following:
- Gathering threat intelligence – Monitoring chatter on social media platforms and discussion forums and monitoring darknet forums can reveal early warnings of protests, planned attacks, or internal sabotage plans. For instance, monitoring Telegram channels and Reddit threads can expose coordinated campaigns against specific companies.
- Event risk profiling – Monitoring public sentiment across social media platforms in a specific community or geographical location can reveal risks surrounding these events and help allocate the required resources to protect them. For instance, tracking hashtag sentiment and geolocation data helps predict crowd behavior and potential disruptions.
- Detect insider threats – Monitoring employees' and vendors' public interactions can reveal their plans to conduct actions against corporate welfare or reveal their associations with hostile groups. LinkedIn activity, public forum participation, and social media connections often indicate potential risks.
- Reveal supply chain vulnerabilities – OSINT can be used effectively to monitor vendors and third-party providers across supply chain networks, which helps reveal partner vulnerabilities, financial instability, or associations with sanctioned entities. Public financial filings, news coverage, and social media monitoring expose vendor weaknesses before they impact business operations.
What are the risks surrounding workplaces and events?
There are different types of risks surrounding corporate works and events; here are the main ones and their different types:
Harassment
Harassment and extremism are increasingly becoming critical concerns in both corporate environments and public event settings. While often viewed separately, they share common features: they are both driven by ideology, personal grievance, or power dynamics, and most of them escalate from digital expressions into real-world threats.
Workspace harassment
Workplace harassment can take many forms, such as verbal, psychological, sexual, or digital. It also has different types:
- Internal threats - For example, disgruntled employees may bully, doxx, or intimidate previous work colleagues. Former employees often use professional networks like LinkedIn and Glassdoor to spread damaging information or coordinate harassment campaigns against their previous employers.
- External harassment - Public-facing staff such as PR, marketing, and HR personnel may become targets of harassment campaigns by former employees or online users. Social media platforms like X, Reddit, and LinkedIn can host or amplify harassment, resulting in damage to individual reputations and organizational trust. Customer service representatives and executives face coordinated attacks when companies make unpopular decisions.
Event-related harassment
On the other hand, event-related harassment involves high-profile speakers, performers, or attendees who may be subjected to coordinated online harassment before, during, or after an event. Examples include:
- Doxxing campaigns - Leaking personal details about the target and posting them online to intimidate them. For example, conference speakers and corporate executives may find their home addresses, family information, and even personal relationships exposed across forums and social platforms.
- Targeted abuse – Spreading threatening messages and malicious rumors via social platforms. Coordinated bot networks amplify negative messaging to create artificial outrage and pressure targets to withdraw from events or to act according to attackers’ agenda.
- Racial abuse - Marginalized individuals or small ethnic groups are often disproportionately targeted, particularly during political and social events. Minority executives and speakers face intensified harassment campaigns that combine professional and personal attacks.
Extremism
While less discussed, extremism within corporate environments is becoming increasingly important. We can differentiate between two types:
Workplace extremism
Corporate environments can contain radicalized individuals who use their positions to advance extremist agendas (e.g., white nationalism, religious extremism, anti-government movements) or recruit colleagues. Employees may leverage company resources, databases, or internal communications to support hostile activities. On the other hand, tensions can flare between employees over political or social issues. Remote work arrangements create additional monitoring challenges as personal and professional digital spaces blend together.
Extremism at public events
Public events are becoming prime targets for extremist groups seeking maximum visibility and disruption. Corporate conferences, product launches, and industry gatherings face threats ranging from coordinated protests to more severe security risks. Extremist groups announce their intentions or share extremist propaganda in advance on forums like 8kun, Telegram, and some darknet forums. They leverage corporate events as recruiting opportunities or platforms to spread their messaging through disruption and media coverage.
The role of OSINT in risk mitigation
OSINT can serve as an early warning system that shifts reactive security approaches to proactive defense strategies. By systematically monitoring and analyzing publicly available information, organizations can detect potential threats months before they develop into actual incidents.
Pre-event intelligence gathering
The most effective OSINT operations begin long before any event occurs. Organizations should establish continuous monitoring of relevant online spaces where threats typically emerge. This includes tracking specific keywords related to the company, key executives, or planned events across multiple platforms, including social media, simultaneously.
For example, we can use Google Dorks to search for any mention of a specific keyword online. Google Alert also lets users know when a particular word or phrase is mentioned anywhere on the surface web.
Here are some Google Dorks for searching for a specific keyword/s online:
"keyword" | This is the most basic dork. It will search for the exact phrase "keyword" anywhere on the surface web.
keyword filetype:pdf | This dork will search for PDF documents that contain the word "keyword." Such dork allows finding reports, whitepapers, or presentations.
intitle:keyword | This dork will search for pages that have the word "keyword" in their title tag.
inurl:keyword | This dork will search for URLs that contain the word "keyword."
site:example.com keyword | This dork limits your search for "keyword" to a specific website, in this case, example.com. Replace example.com with the actual site you want to search, such as LinkedIn.com or Glassdoor.com.
site:pastebin.com "CompanyName Event" | Find exposed event documents on Pastebin website.
For corporate events, monitoring should intensify at least 20 days before the scheduled date. Threat actors often discuss their plans in advance, particularly on platforms like Telegram, Discord, or specialized forums. Security teams can track mentions of event locations, speaker names, or company-specific hashtags to identify brewing controversies or planned disruptions.
Here are some resources to start your search:
- Teleteg - A Telegram search engine
- Lyzem - Another Telegram search engine
- DiscordServers, Discord.me, top.gg and Discadia are directories for listing Discord web servers
- Social Searcher - A social media search engine
- Wayback Machine - Find archived versions of web pages mentioning your company or event
Real-time threat detection
During active events or high-risk periods, OSINT capabilities are shifted to real-time monitoring. This involves tracking live social media feeds, news coverage, and communication channels for immediate threats or escalating situations.
Geographic intelligence becomes particularly valuable during public events. Monitoring location-based posts, check-ins, and geotagged content helps security teams understand crowd dynamics and identify potential flashpoints. When protests or demonstrations occur near corporate facilities, real-time social media monitoring reveals crowd size, mood, and movement patterns.
Here are some tools and online services for real-time social media and news monitoring:
- LiveUAmap - Provides real-time geopolitical incident mapping across different countries worldwide, such as Ukraine, Syria and Israel (see Figure 1).
- Hoaxy - Visualize the spread of information on X
- Maphub - Create interactive maps
- Google News - Aggregate news from thousands of sources worldwide
- Gdeltproject - The GDELT Project tracks global broadcast, print, and online news sources across nearly every country worldwide, covering more than 100 languages
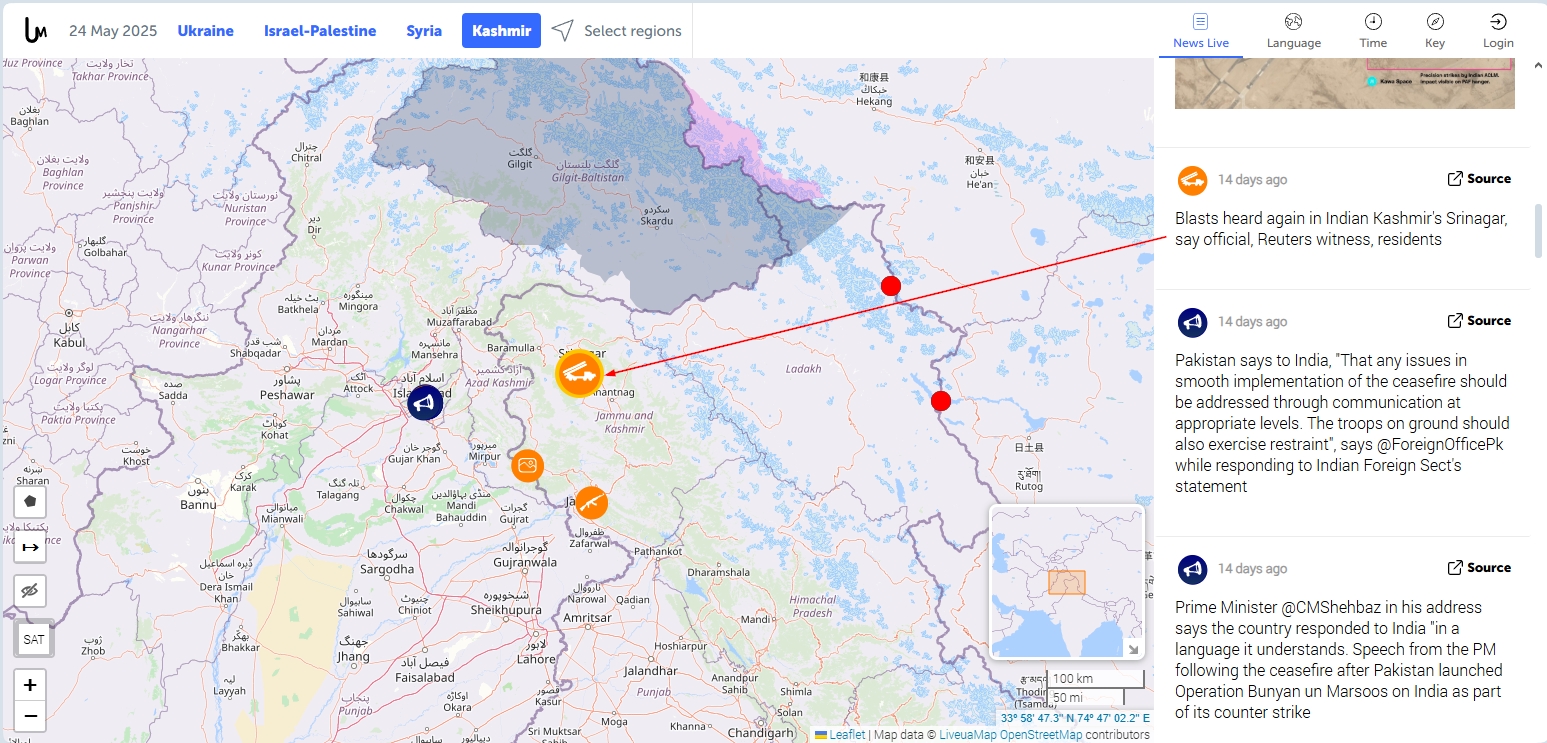
Figure 1 - LiveUAmap shows geopolitical events in tense locations worldwide
OSINT has evolved into an essential component of modern corporate security strategies. The tools and techniques outlined in this guide provide organizations with practical methods to monitor threat landscapes across multiple platforms without dedicating too much investment. However, implementing effective OSINT capabilities requires more than deploying monitoring tools. Organizations must establish clear procedures for identifying threats and assessing their potential impact on its operations. The most sophisticated monitoring systems fail without proper integration into existing security protocols.
Corporate security teams that ignore publicly available intelligence operate with unnecessary blind spots. Threat actors consistently spread their intentions through digital channels, providing organizations with opportunities to prevent incidents rather than merely respond to them. OSINT represents a shift from reactive security postures to predictive threat management that protects people and events more effectively.
Gather intelligence quickly and securely
Are you taking your investigation into adversary territory? Maintaining anonymity, security and compliance is a major challenge and homespun solutions can drain resources from mission-critical work.
Silo is a digital investigations platform purpose-built to support, streamline and secure the most sensitive research. Many analysts from top federal agencies and enterprises rely on managed attribution to control your digital fingerprint and appear in-region to foreign websites. To learn more about how to protect your investigation and fast track collection, read more about Silo or start a free trial.
Tags OSINT research